This is not going to be a complete guide on how to setup SAML-authentication for VPN on the ASA we will only cover the SAML-configuration on the ASA and not the configuration of basc VPN-settings like Group Policies etcWe will also not cover the configuration of the IdP mainly because 1 you the network administrator will probably not be the one tasked to do that configuration and 2. My guide to setting up Windows Server 2019 for VPN with no guarantees that it will work By Michael Niehaus on April 27 2020 3 Comments Sadly I can remember setting up my first Remote Access Service RAS on Windows NT Server 40.

Array Networks Ssl Vpn Integration With Authpoint
Virtual private networks may be classified by several categories.

How does vpn authentication work. MFA is a core component of a strong identity and access management IAM policy. VPN security is only as strong as the methods used to authenticate the users and the devices at the remote end of the VPN connection. User request acts as an authentication request to RADIUS ServerminiOrange.
VPN services hide a given users IP address and hence make any online communications. Once you obtain a root certificate you upload the public key information to Azure. VPN is a Virtual Private Network that allows a user to connect to a private network over the Internet securely and privately.
How Does a VPN Work. What is Multi-Factor Authentication MFA. Currently only ASCII characters are supported for RADIUS shared secrets - Unicode characters will not work.
VPN creates an encrypted connection known as VPN tunnel and all Internet traffic and communication is passed through this secure tunnel. Multifactor authentication MFA is a security system that requires more than one method of authentication from independent categories of credentials to verify the users identity for a login or. When testing the VPN I connected to all US streaming servers one by one and checked to see if I could access the US Netflix library.
Refer to this document for more information on integrating with client VPN. Does RADIUS authentication work with both IKEv2 and SSTP VPN. This allows VPN traffic to remain private as it travels between devices and the network.
The MX does not support mapping group policies via Active Directory for users connecting through the client VPN. When using Azure for certificate authentication the Azure VPN gateway performs the validation of the certificate. For years enterprises have relied on virtual private networks to offer remote access to their internal applicationsSince VPNs offer a private and encrypted connection for a remote user to connect to applications its quickly evolved as an integral part of providing.
You can also specify list of revoked certificates that shouldnt be allowed to connect. I also had the problem of no valid certificates available for authentication although it only prompted once rather than a flood like the OP. Unfortunately it failed every time as discussed in our guide on using AVG with Netflix.
It uses a public-key cryptography technique to authenticate between client and server. Streaming Does AVG VPN work with Netflix Other VoD Services. Learn how VPNs work decide if you need one.
Any OTP solution that serves as a RADIUS server should work though really. Simple authentication methods based on static passwords are subject to password cracking attacks eavesdropping or even social engineering attacks. Over VPN - Use the IP address of the MXZ1 on the highest-numbered VLAN in VPN.
When you open the client or go to portaldukeedu youll see a drop-down menu of departmental VPNs. Types of VPN. The certificate used for authentication was issued by my internal CA to the Computer NOT the user.
A VPN or Virtual Private Network is a private connection over the Internet that secures your WiFi connection and helps protect your online privacy. No AVG does not with Netflix. This type provides access to an enterprise network such as an intranetThis may be employed for telecommuting workers who need access to private resources or to enable a mobile worker to access important tools without.
Primary authentication initiates with the user submitting his Username and Password for Fortinet Fortigate. Secure VPN Connection terminated locally by the Client. SSH uses a client-server architecture for secured communication over the network by connecting an ssh client with the ssh server.
Most library resources are available from off-campus through the EZProxy serviceno VPN connection is necessary. Anonymous authentication is the simplest type of user authentication. Virtual Private Network VPN is a remote access technology that creates a private encrypted connection over the Internet between a single host and Stanfords private network SUNet.
However the cause and solution for my problem was. Stanfords VPN allows you to connect to Stanfords network as if you were on campus making access to restricted services possible. A Virtual Private Network VPN is a tool that enables online users to connect to a secure and private network over the public internet.
However it does break the seamless and transparent nature of DirectAccess which are key advantages over traditional client-based VPN. There are two types of VPN available. You need to upload your certificate public key to the gateway.
A virtual private network VPN extends a companys network allowing secure remote user access through encrypted connections over the Internet. Online consumers may not understand what is a VPN but nevertheless use VPN services and various VPN protocols to gain anonymity and data security in the online world. As for multifactor authentication providers that work with DirectAccess both the Entrust and Gemalto solutions are popular and work well.
Multi-factor Authentication MFA is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application online account or a VPN. Remote access A host-to-network configuration is analogous to connecting a computer to a local area network. Many reported they can now work from home or use a single machine to access VPN instead of two machines or simply made their life much simpler.
Certificates are used by Azure to authenticate clients connecting to a VNet over a Point-to-Site VPN connection. Understand how IPsec and SSL VPNs differ and learn how to evaluate the secure remote computing protocols based on performance risk and technology implementation. How does it work.
The root certificate is then considered trusted by Azure for connection over P2S to the virtual network. Create and enter a RADIUS Shared Secret make note of this secret - we will need to add this to the Dashboard. Did you know the global VPN virtual private network market is forecast to reach 7559 billion US.
Only one AD server can be specified for authentication with AnyConnect at the moment. If a user set by anonymous authentication exists for Virtual Hub anyone who knows the user name can connect to the Virtual Hub and conduct VPN communication. If your department doesnt have a separate VPN select Default if it does select your department by name.
By default ssh server listens to the standard TCP port 22 you can change this for better security. After the first level of authentication miniOrange prompts the user with 2-factor authentication and either grantsrevokes access based on the input by the user.

Cookbook Fortiauthenticator 6 1 0 Fortinet Documentation Library
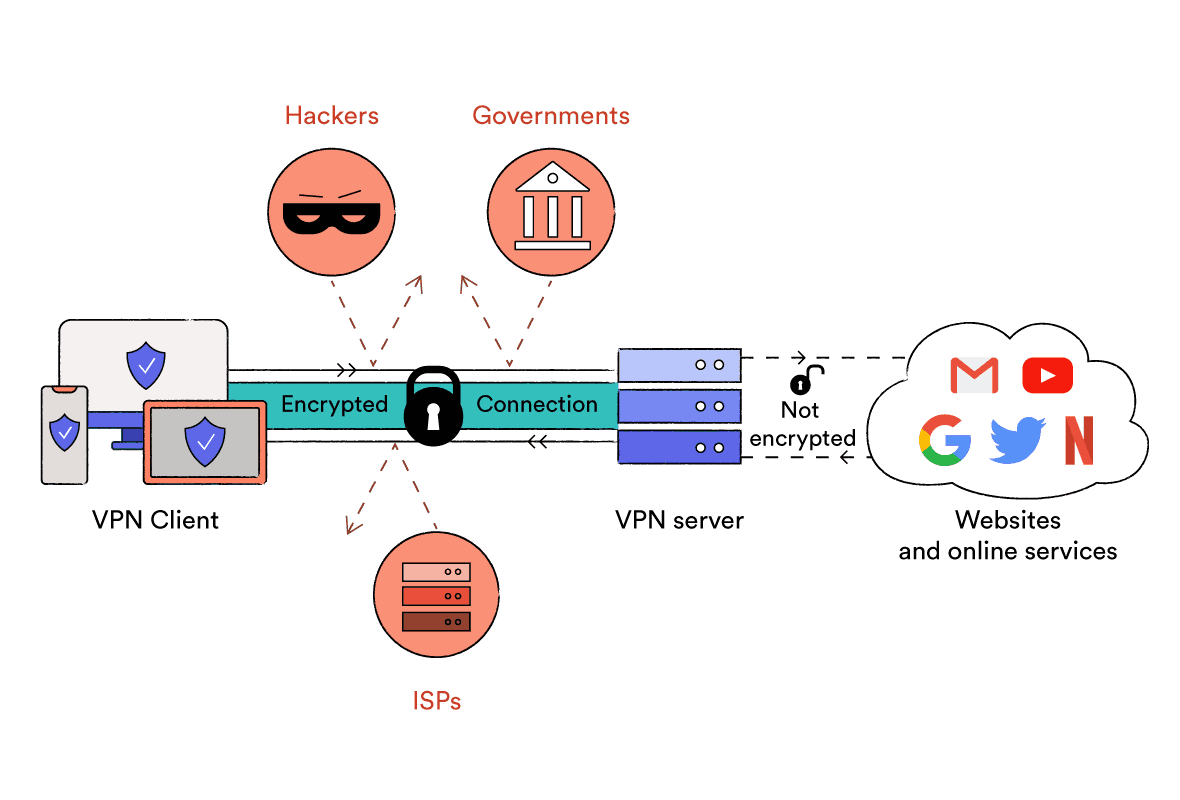
How Do Vpns Work Vpn Encryption Tunneling Explained
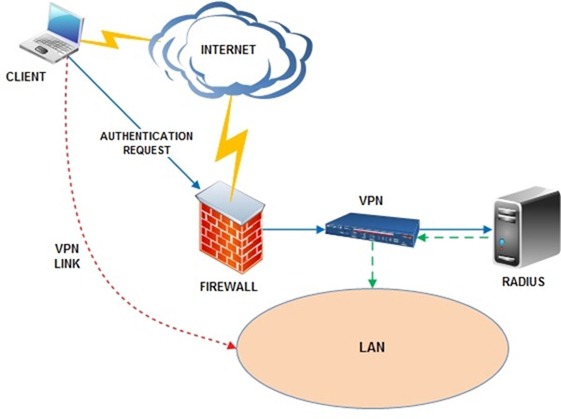
Setup Nps For Radius Authentication In Active Directory Nolabnoparty
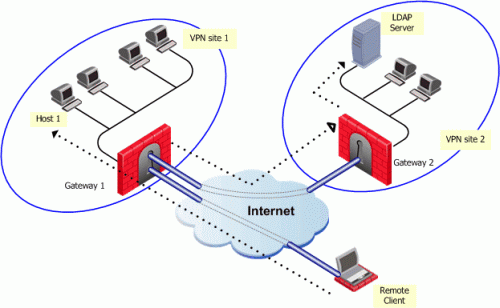
Working Of Vpn Using Ldap Authentication Download Scientific Diagram
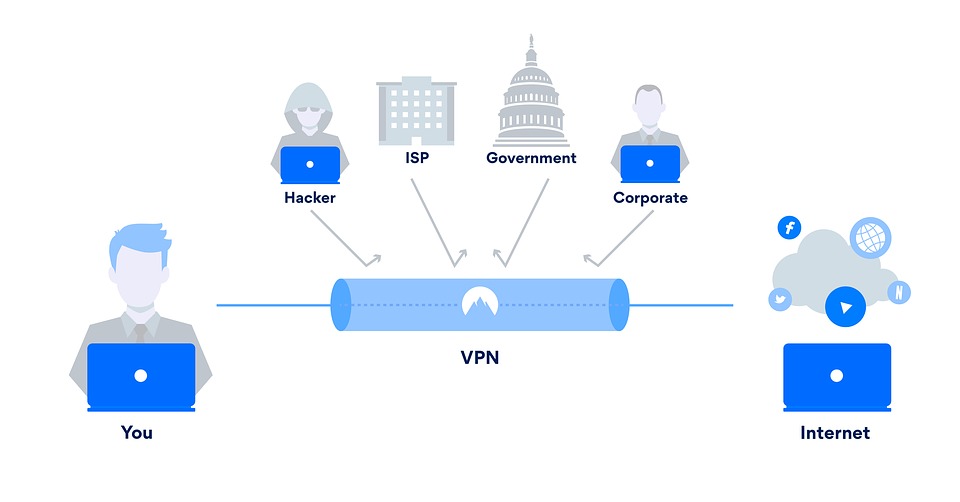
How Do Vpn Encryption Protocols Work At T Cybersecurity

Authenticate Aws Client Vpn Users With Saml Networking Content Delivery
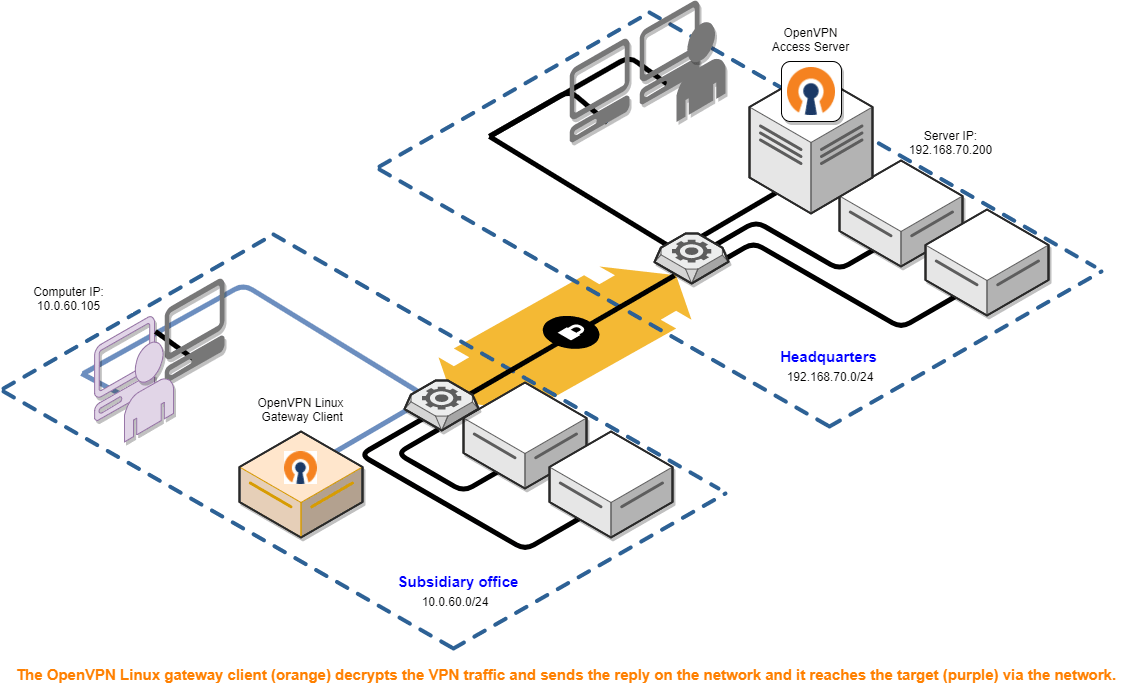
Site To Site Vpn Routing Explained In Detail Openvpn
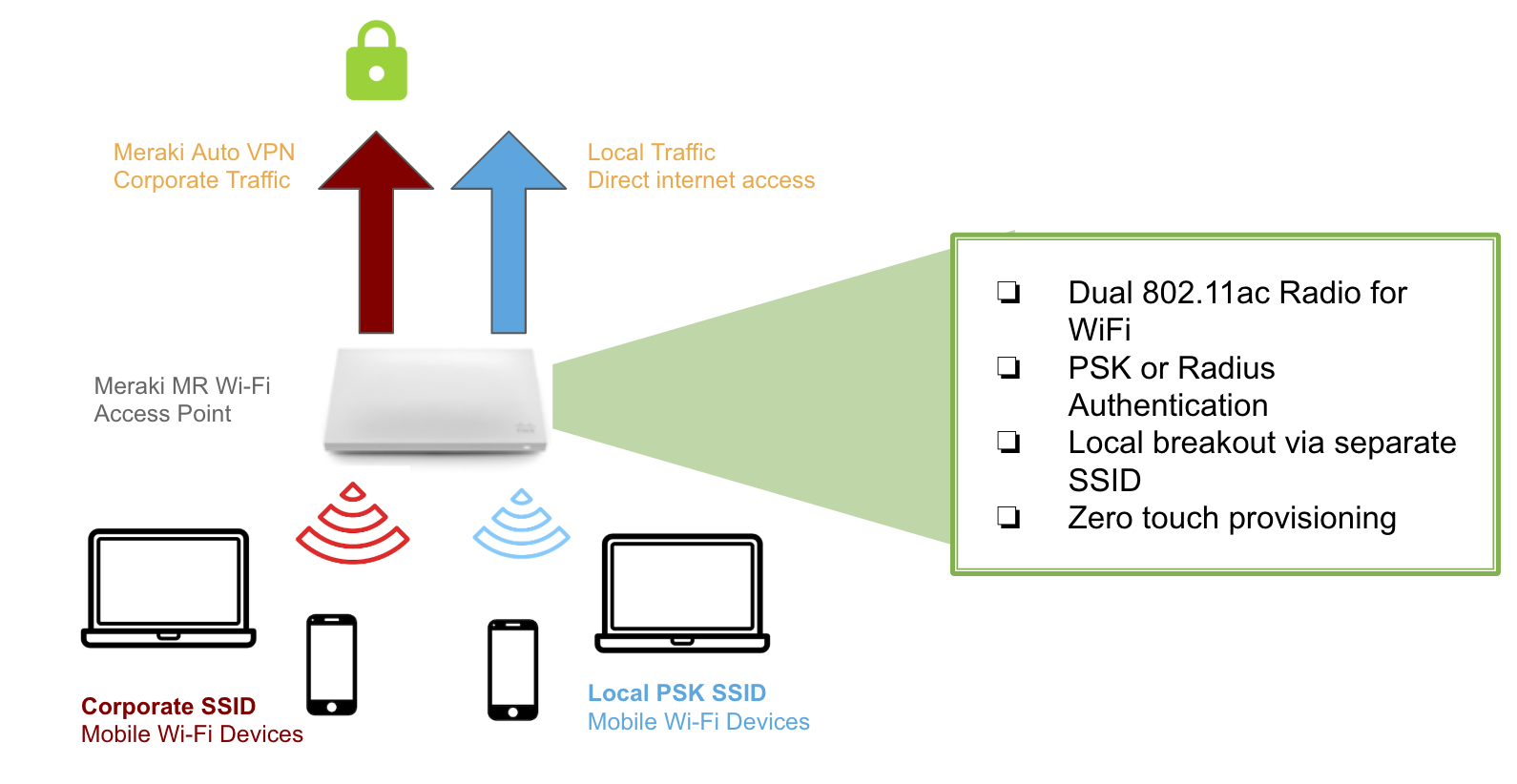
Mr Teleworker Vpn Cisco Meraki
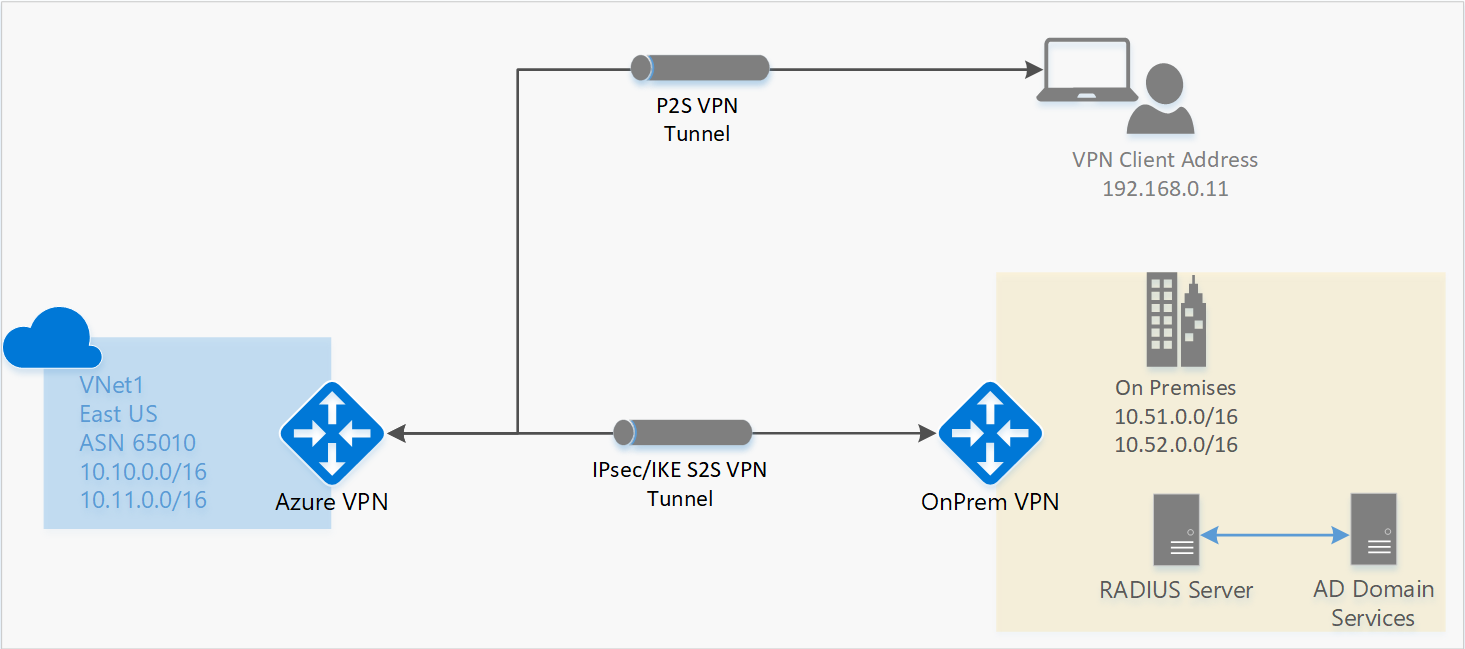
Connect A Computer To A Virtual Network Using Point To Site And Radius Authentication Powershell Azure Vpn Gateway Microsoft Docs
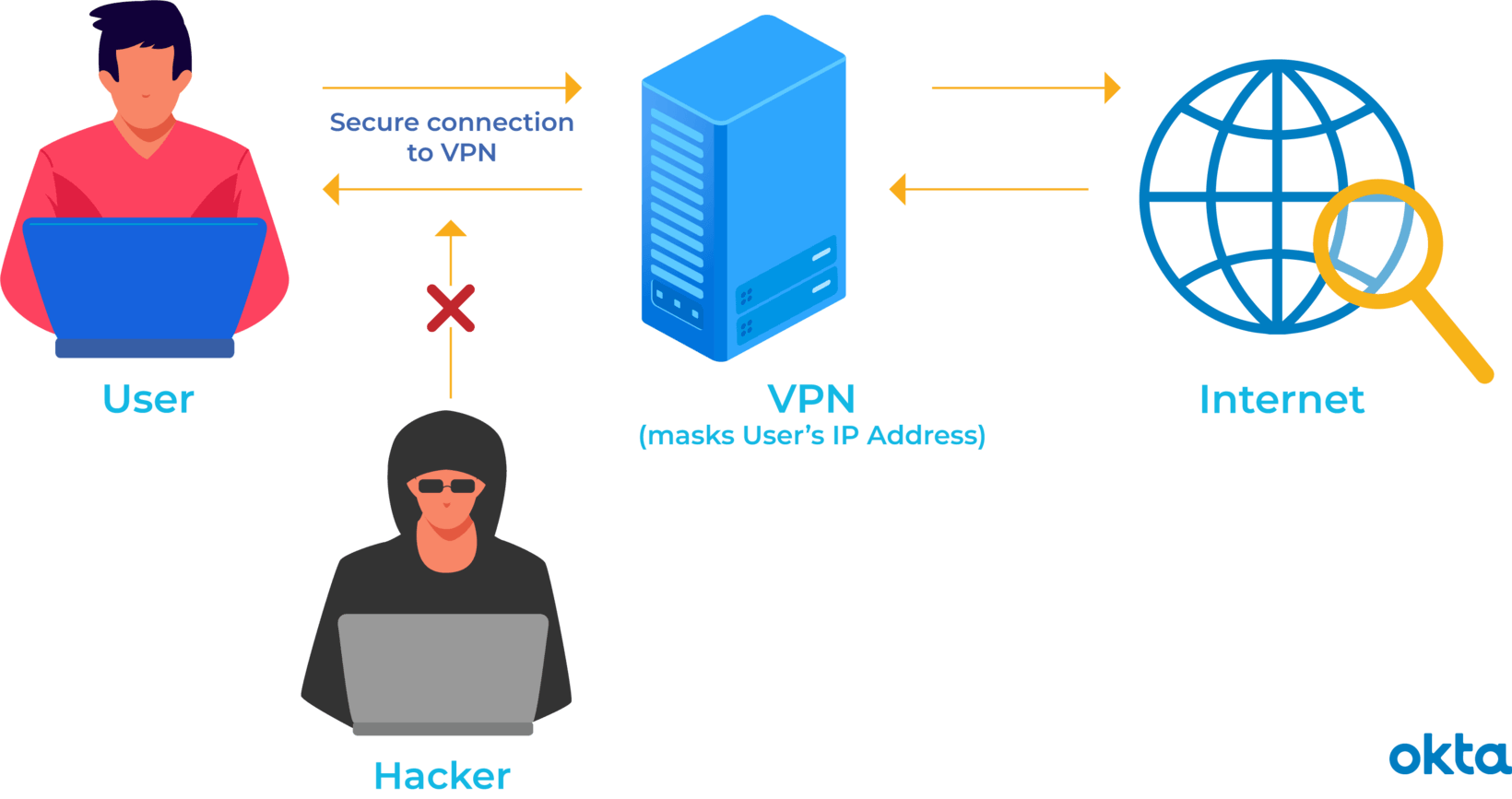
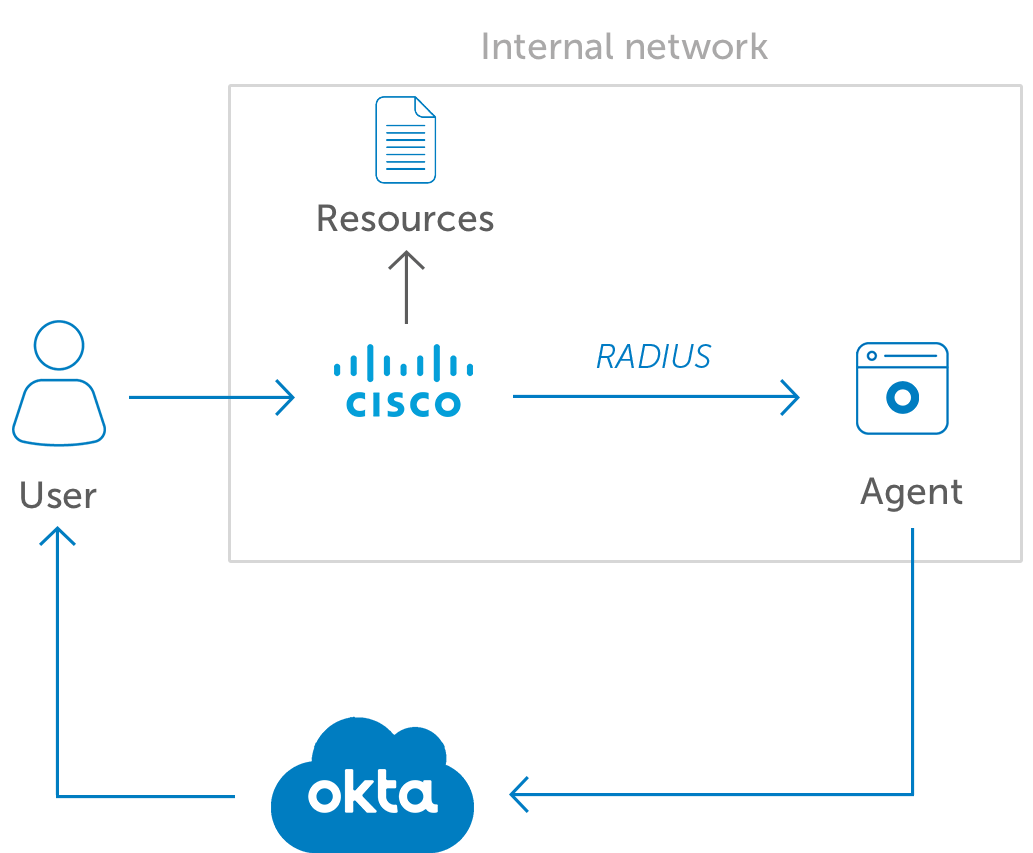
What Is A Vpn How Does It Work Okta Singapore
2 2 User Authentication Softether Vpn Project
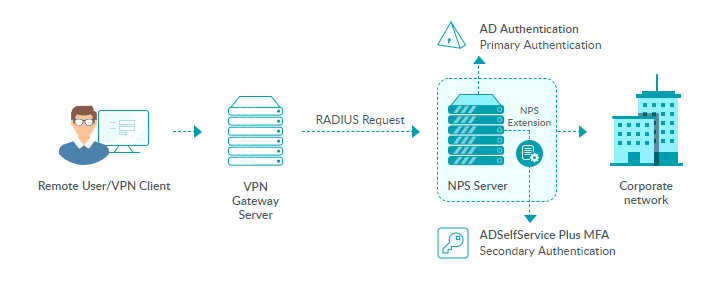
How To Enable Mfa For Vpn Logins And Radius Supported Endpoint Logins
2 2 User Authentication Softether Vpn Project

Vpn And Conditional Access Windows 10 And Windows 11 Windows Security Microsoft Docs

Always On Vpn Overview The Now Micro Blog

Virtual Private Network Wikipedia

Implementing Vpn Split Tunneling For Office 365 Microsoft 365 Enterprise Microsoft Docs
Post a Comment
Post a Comment